Infrastructure - Development - Digital
client-server vs peer-to-peer
mobility vs office
network types by area
summary
Network
introduction
signal transmission media
protocols and services
addresses
hardware components
summary
Operating Systems
hardware resources
workstations vs servers
open-source vs proprietary
terminology
Directory services
domain accounts
permissions
solutions
the Web
topology
DNS
hosting
languages and protocols
Content Delivery Network
OS virtualisation
principle and motivations
possibilities
editors and solutions
Cloud
concepts
a few big names
types of resources
benefits and points of concern
IoT and beacons
introduction
introduction
communication technologies
Telephony
VOIP / TOIP / POTS
VOIP technology
VOIP solutions
mobile technologies
Entreprise Mobility Management (EMM)
Security
threats
controls
recovery
CIA Triad (confidentiality, integrity, availability)
Wifi authentication and encryption
cryptology
digital certificates
proxy and firewalls
Virtual Private Network (VPN)
Network Access Control (NAC)
Role-based Access Control (RBAC)
types of networks
topologies
peer-to-peer vs client-server
by area
transmission media
ethernet cables
radio waves
WiFi
optical
encoding methods
Packet Tracer introduction
addressing
unicast, multicast, broadcast
MAC
IP
basic principles
network mask
network ID and broadcast address
network size
early Internet and classes
private vs public and NAT
the 10 commandments
packet Tracer
example and
exercises
answers to subnetting exercises
subnetting exercise
VLSM
exercises
answers to exercises
IPv6
hardware
router
switch
WiFi
wiring
Packet
Tracer
WAN
xDSL and user equipment
local loop / telecom / ISP equipment
Autonomous Systems
IPv4 and IPv6 address allocation by RIRs
routing
principle
Packet Tracer exercise
correction
supernetting and route aggregation
troubleshooting
Packet Tracer
exercise correction
dynamic routing
protocols
IPv6
protocols
definition
ethernet
spanning tree
WiFi data transfer
IPv4
IPv6
TCP / UDP
Applications: protocols and ports
DNS
DHCP
FTP
email
troubleshooting
network management
Packet
Tracer
Delay/Disruption Tolerant Network (DTN)
OSI model
full
TCP/IP
example
from client to server Interactive Content
more protocols
Network functions
multilayer switch
protocol firewall
proxy
Networks interconnection
NAT and PAT
VLAN
VPN
IPv4 to IPv6 transition
Packet capture with Wireshark
introduction
filters
traffic
capture examples
Traffic engineering
definition
performance parameters
network management and automation
overlay networks
WiFi mesh networks
layer 7 switching
TCP acceleration
content
delivery network
Going further
CISCO netacad
trends in networking
impact of up-coming technologies
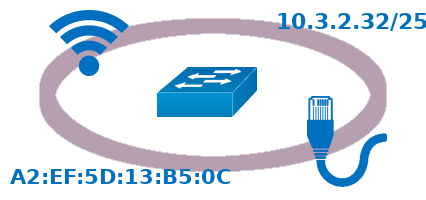
Routers and switches
CISCO hardware
IOS (operating system)
working principle
Router configuration
Switch configuration
Secure access
backup and restore
VLAN
principle
configuration
management
Routing
static
dynamic
L3
switch
DHCP
router runs the service
router runs relay agent
ACL / NAT
ACL basics
the wildcard mask
standard ACL
extended ACL
named ACL
troubleshooting
NAT
configuration
DMZ
IPv6
IPv6 router addressing
IPv6 routing
Spanning Tree Protocol
principle
implementation
Etherchannel
principle
configuration
VPN
IPsec principles
configuration
QoS
principles
example (VOIP / web)

